The reliable anti-tailgating way of a vehicle barrier system
Recently, many paid garages have converted to fully automated facilities. Whereas in the past there were human attendants at every exit lane, full automation allows landlords to eliminate the human component by installing payment devices called Pay On Foot (POF) machines. Customers take a ticket upon entry, pay at a POF machine when leaving, insert the paid ticket into the exit terminal, and proceed to leave when the system recognizes the paid ticket and opens the gate arm. Full automation allows for an elimination of exit lane labor costs, reduced transaction times at exits, and elimination of mistakes or potential fraud.
Despite the benefits of a fully automated facility, certain problems exist when there is no human oversight at exit lanes. One problem that is increasingly common is for non-paying cars to follow a paying car into (or out of) the facility. This is referred to as “tailgating,” and allows the tailgating car(s) to avoid paying. Embodiments of the present disclosure address these and other issues.
The embodiments of the present disclosure provide a vehicle barrier system that may be used to help prevent instances of “tailgating,” where non-paying cars closely follow a paying car into (or out of an automated garage facility or other venue to avoid fees. A vehicle barrier system according to various aspects of the present disclosure includes: a sensor system for detecting a vehicle seeking passage through a gateway; a first gate system; a second gate system subsequent to the first barrier gate system; and a control system in communication with the sensor system, the first gate barrier system, and the second barrier gate system. The control system comprises: a processor; and memory coupled tothe processor and storing instructions that, when executed by the processor, cause the control system to: receive data from the sensor system indicating the presence of the vehicle; in response to receiving the sensor data indicating the presence of the vehicle, determine whether the second gate system is closed; in response to determining that the second gate system is closed: open the first gate system to allow the vehicle to pass the first gate system; and attempt to close the first gate system behind the vehicle after the vehicle passes the first gate system; in response to successfully closing the first gate system behind the vehicle, opening the second gate systemto allow the vehicle to proceed through the gateway; and in response to unsuccessfully closing the first gate system behind the vehicle, generating an alarm.
The present disclosure includes various methods, apparatuses (including computer systems) that perform such methods, and computer readable media containing instructions that, when executed by computing systems, cause the computing systems to perform such methods. Other features will be apparent from the accompanying drawings and from the detailed description which follows.
Brief description of drawings
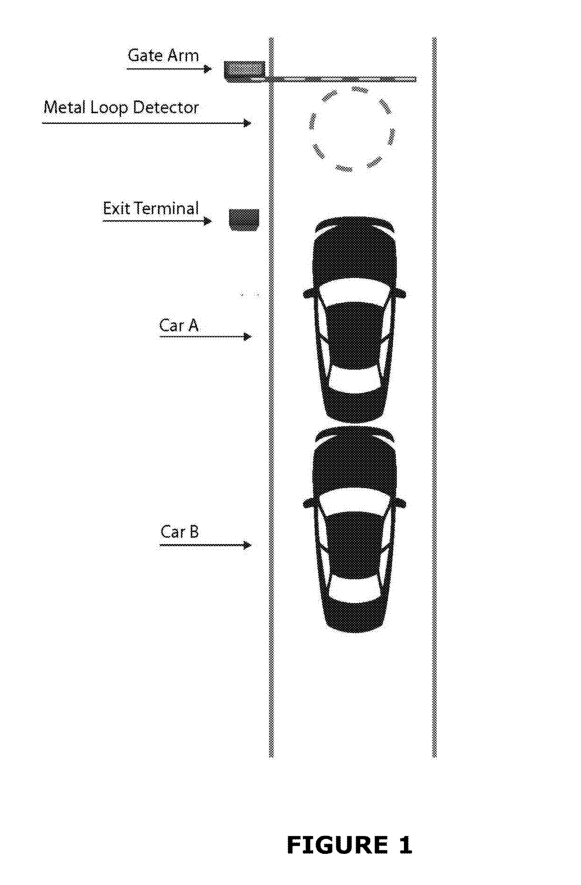
FIG.1 illustrates an exemplary tailgating scenario.
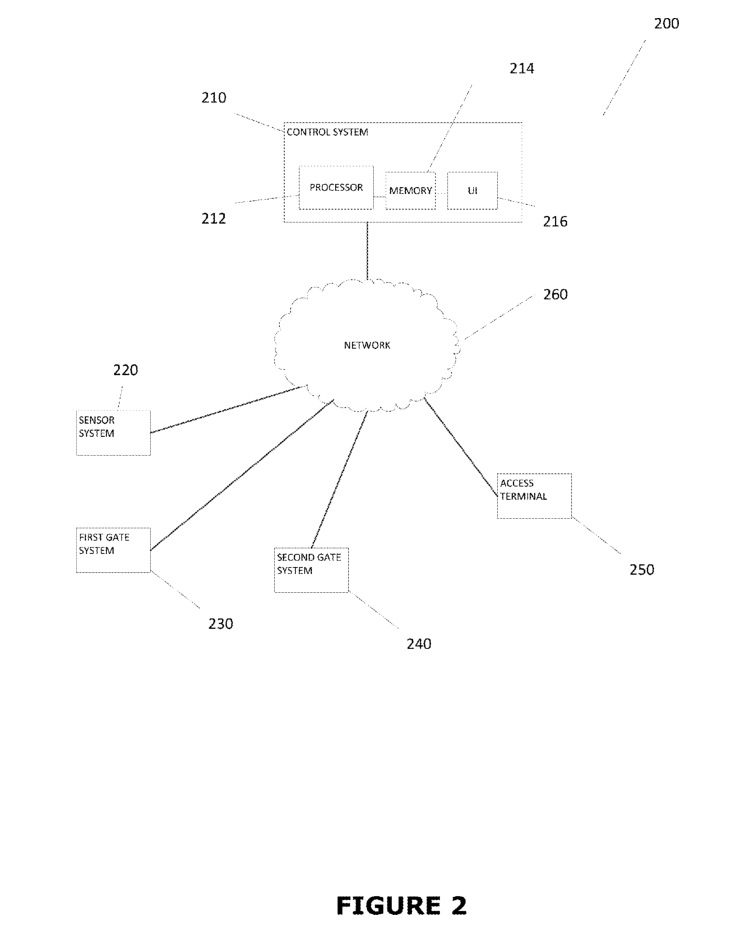
FIG.2 depictsa block diagram of an exemplary system according to various aspects of the present disclosure.
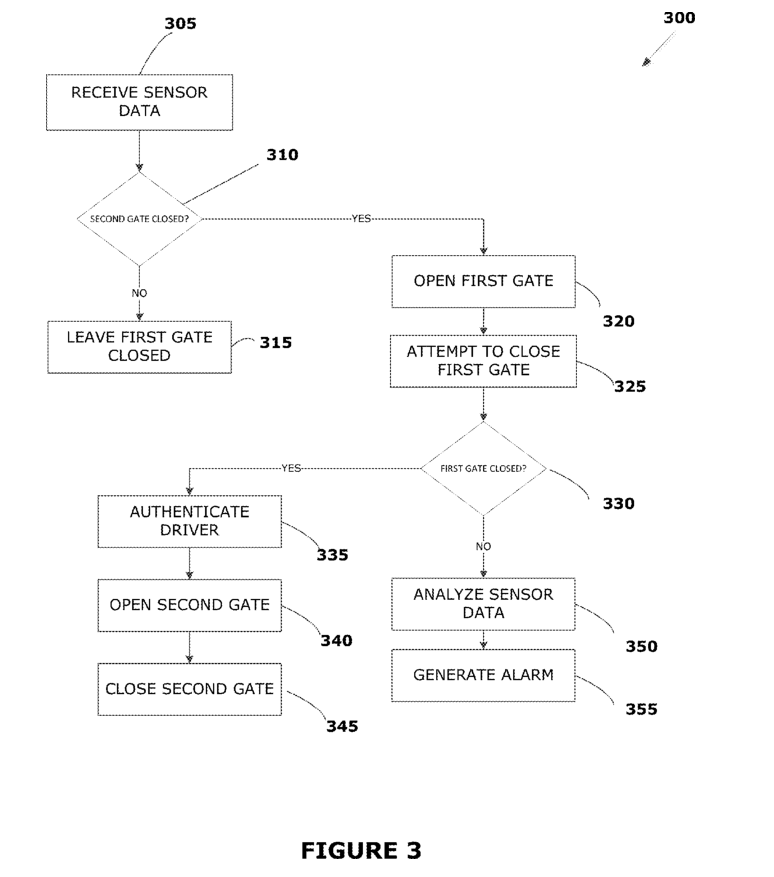
FIG.3 illustrates an exemplary method according to various aspects of the present disclosure.
FIGS. 4A and 4B illustrate an overhead view of an exemplary embodiment ofthe system in FIG.2 in operation.
How does a vehicle barrier system to anti-tailgating?
Subject matter will now be described more fully Hereinafter with reference to the accompanying drawings, which form a part hereof, and which show, by way of illustration, specific example embodiments. Subject matter may, however, be embodied ina variety of different forms and, therefore, covered orclaimed subject matter is intended to be construed as not being limited to any example embodiments set forth herein; example embodiments are provided merely to be illustrative. Likewise, a reasonably broad scope for claimed or covered subject matter is intended. Among other things, for example, subject matter may be embodied as methods, devices, components, or systems. Accordingly, embodiments may, for example, take the form of hardware, software, firmware or any combination thereof (other than software per se). The following detailed description is, therefore, not intended to be taken ina limiting sense.
In the accompanying drawings, some features may be exaggerated to show details of particular components (and any size, material and similar details shown inthe figures are intended to be illustrative and not restrictive).
Therefore, specific structural and functional details disclosed herein are not to be interpreted as limiting, but merely asa representative basis for teaching one skilled in the art to variously employ the disclosed embodiments.
Reference in this specification to “one embodiment” or“an embodiment” means that a particular feature, structure, or characteristic described in connection with the embodiment is included in at least one embodiment of the disclosure. The appearances of the phrase “in one embodiment” in various places in the specification are not necessarily all referring to the same embodiment, nor are separate or alternative embodiments mutually exclusive of other embodiments. Moreover, various features are described which may be exhibited by some embodiments and not by others. Similarly, various requirements are described which may be requirements for some embodiments but not other embodiments.
Any combination and/or subset of the elements of the methods depicted herein may be combined with each other, selectively performed or not performed based on various conditions, repeated any desired number of times, and practiced in any suitable order and in conjunction with any suitable system, device, and/or process. The methods described and depicted herein can be implemented in any suitable manner, such as through software operating on one or more computer systems. The software may comprise computer-readable instructions stored in a tangible computer-readable medium (such as the memory of a computer system) and can be executed by one or more processors to perform the methods of various embodiments.
FIG.1 illustrates an example of “tailgating” at a conventional parking checkpoint. Whenthe two cars (Car A and Car B) are close enough to each other, the sensor system (i.e., the Metal Loop Detector embedded under the pavement) prevents the Gate Arm from closing on Car B after the driver of Car A pays for parking at the Exit Terminal. Instead, the Gate Arm is left in the open (raised) position to prevent it from coming downon Car B and causing damage, thus allowing Car B to follow Car A under the Gate Arm without paying at the Exit Terminal. Additionally, there is typically a delay in gate arms coming down simply due to the mechanical speed of the equipment. Even if the Gate Arm started to lower to a closed position, if the Metal Loop Detector detects the presence of a vehicle (i.e., Car B) under the Gate Arm, the system will raise the Gate Arm back to open position, allowing Car B to exit without having to insert an unpaid ticket at the Exit Terminal.
FIG.2 is a block diagram ofan exemplary vehicle barrier system for preventing tailgating according to aspects of the present disclosure, while FIG.3 illustrates an exemplary method for preventing tailgating that may be practiced in conjunction with thesystem in FIG. 2. FIGS. 4 A and 4B illustrate an exemplary embodiment ofthe system in FIG.3 in operation. Embodiments ofthe present disclosure may be utilized to control access to or from a parking garage, parking lot, or other venue.
While FIG.2 illustrates various components of a computer system, it is not intended to represent any particular architecture or manner of interconnecting the components. Other systems that have fewer or more componentsmay also be used. In FIG. 2, the system 200 includes a control system 210 comprising a processor 212, memory 214, and user interface 216. Control system210 may include any number of different processors, memory components, and user interface components, and may interact with any other desired systems and devices in conjunction with embodiments ofthe present disclosure.
The functionality of the control system 210, including the steps of method 300 from FIG.3 described herein (in whole or in part), may be implemented through the processor 212 executing computer-readable instructions stored in the memory 214 of the control system 210. The memory214 may store any computer-readable instructions and data, including software applications, applets, and embedded operating code. Portions of the functionality of the methods described herein may also be performed via software operating on one or moreofthe other components shownin FIG. 3, as well as using additional computing devices.
The functionality of the control system210 or other system and devices operating in conjunction with embodiments of the present disclosure may also be implemented through various hardware components storing machinereadable instructions, such as application-specific integrated circuits (ASICs), field-programmable gate arrays (FPGAs) and/or complex programmable logic devices (CPLDs). Systems according to aspects of certain embodiments may operate in conjunction with any desired combination of software and/or hardware components.
In the example shown in FIG. 2, the processor 212 retrieves and executes instructions storedinthe memory 214 to perform the functionality of the control system 210. Any type of processor, such as an integrated circuit microprocessor, microcontroller, and/or digital signal processor (DSP), can be used in conjunction with embodiments of the present disclosure. A memory 214 operating in conjunction with embodiments ofthe disclosure may include any combination of different memory storage devices, such as hard drives, random access memory (RAM), read only memory (ROM), FLASH memory, or any other type of volatile and/or nonvolatile memory. Data can be stored in the memory 214inany desired manner, such as ina relational database.
The control system 210 includes a user interface 216 that may include any number of input devices (not shown) to receive commands, data, and other suitable input. The user interface 216 may also include any number of output devices (not shown) to provides the user with data, notifications and alerts, and other information. Typical I/O devices may include mice, keyboards, modems, network interfaces, printers, scanners, video cameras and other devices.
The control system 210 may communicate with one or more computing devices, as well as other systems and devices in any desired manner, including via network 260. The control system210 and/or other computing devices may be, include, or operate in conjunction with, a laptop computer, a desktop computer, a mobile subscriber communication device, a mobile phone, a personal digital assistant (PDA), a tablet computer, an electronic bookorbook reader, a digital camera, a video camera, a video game console, and/or any other suitable computing device.
The network 260 may include any electronic communications system or method. Communication among components operating in conjunction with embodiments of the present disclosure may be performed using any suitable communication method, such as, for example, a telephone network, an extranet, an intranet, the Litemet, point of interaction device (point of sale device, personal digital assistant (e.g., iPhoneB, Palm Pilots, BlackberryB), cellular phone, kiosk, etc.), online communications, satellite communications, off-line communications, wireless communications, transponder communications, local area network (LAN), wide area network (WAN), virtual private network (VPN), networked or linked devices, keyboause and/or any suitable communication or data input modality. Systems and devices ofthe present disclosure may utilize TCP/IP communications protocols as well as IPX, Appletalk, IP-6, NetBIOS, OSI, any tunneling protocol (e.g. IPsec, SSH), orany number of existing or future protocols.
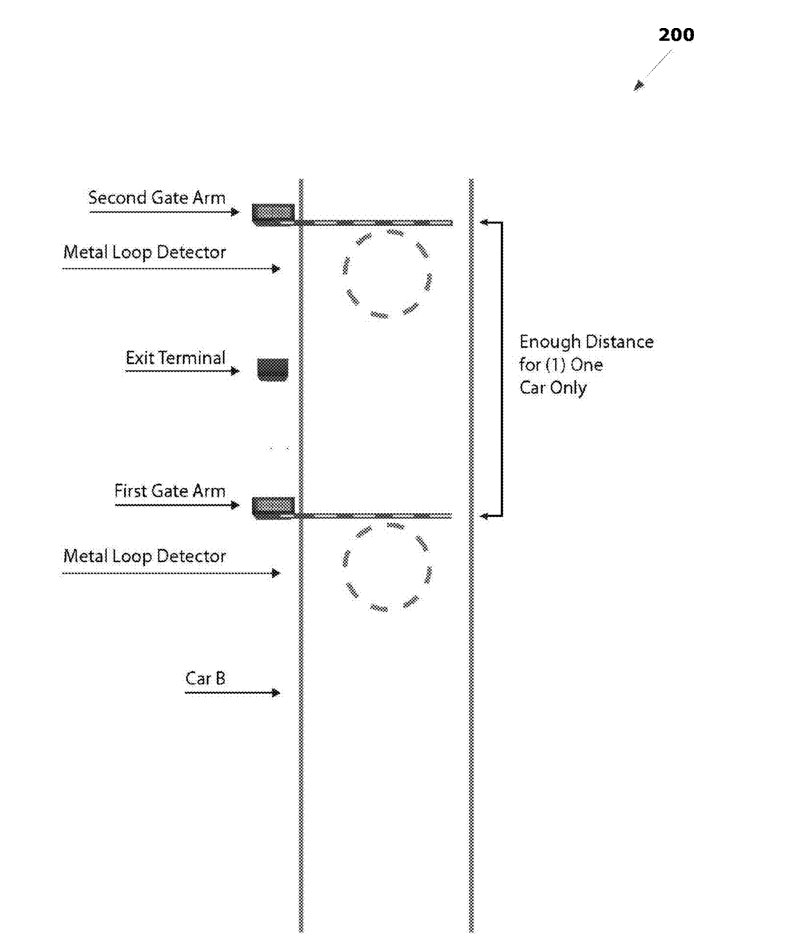
The exemplary vehicle barrier system 200 shown in FIG.2 includesa sensor system 220 in communication with the control system 210. The sensor system 220 may include any number and type of different sensors to detect the presence of vehicles seeking passage througha gateway and to collect other data. Such sensors may include: a camera,a motion sensor,a pressure sensor, and an inductive loop sensor. i the exemplary embodiment ofthe system200 shown in FIG. 4A, the sensor system 220 includesa pair of inductive loop sensors (each labeled “Metal Loop Detector”), with each loop sensor positioned in front of the two gate arms to detect the presence of a vehicle.
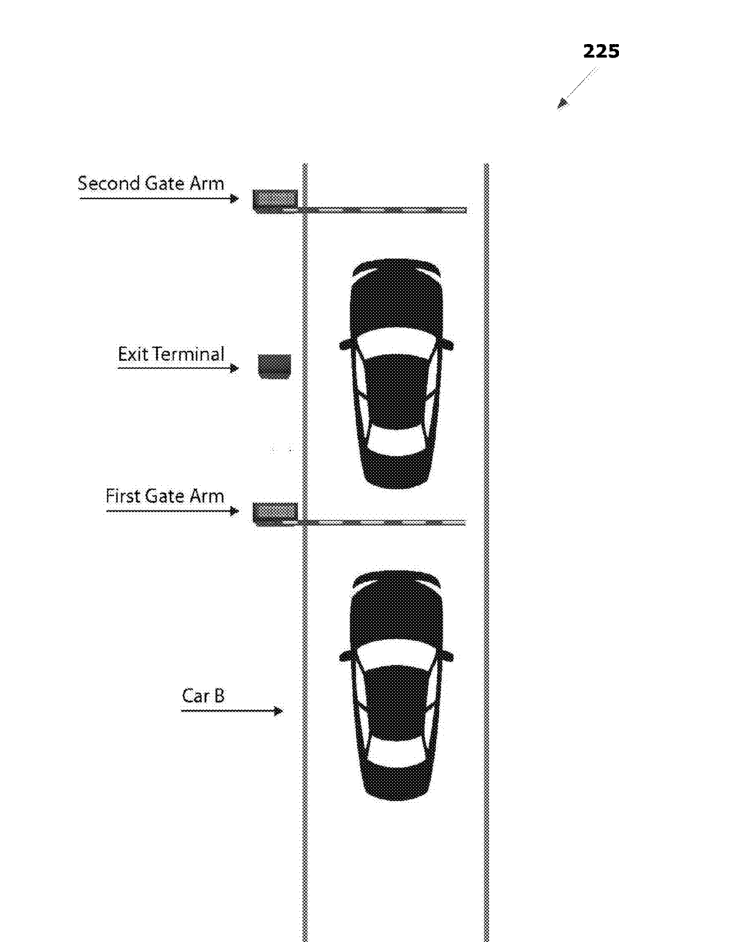
System 200 further includesa pair of gate systems, first gate system 230 and second gate system 240. The first gate system 230 is positioned to control access to an initial portion of a gateway, while the second gate system is 240 is positioned subsequent tothe first gate system 240 to control final access to the gateway. As shown in FIG. 4A, for example,a vehicle first must pass the first gate system 230 (labeled “First Gate Arm”) before passing the second gate system 240 (labeled “Second Gate Arm”).
The Gate Systems 230, 240 may include any numberand type of different doors, gates, and other systems for controlling access toa gateway. For example, Gate Systems 230, 240 may comprise one or more of:a horizontally tilting door,a vertically tilting door,a sectional door,a vertically rotating arm, horizontally rotating arm,a spike barrier, and a post. The first gate system230 and second gate system240 need not utilize the same type of access control system. In the example shownin FIG. 4A, the first gate system 230 and second gate system 240 each includea vertically rotating arm that lowers (closes) to block access to the gateway and raises (opens) to allowa vehicle to pass.
In the example shown in FIG. 2, the Control System 210 is in communication with an Access Terminal 250 adapted to receive input froma driver ofa vehicle. The Access Terminal 250 may be positioned in any desired location, such as next to the first gate system 230 or (as shown forthe “Exit Terminal” in FIG. 4A) next to the second gate system 240. Alternate embodiments may utilize multiple access terminals as well. Li some embodiments, Access Terminal 250 may be adapted to communicate automatically with one or more systems and/or devices associated witha vehicle without input from the driver. For example, the Access Terminal 250 may communicate with a radio frequency identification (RFID) system coupled to a vehicle to automatically authenticate the vehicle for passage through the gateway. A user may also provide input to the Access Terminal 250 by scanning an RFID badge, inserting a validation ticket, entering a code, scanning a barcode, and/or entering biometric information.
The Control System210 may be adaptedto analyze the information collected from the user (or automatically from a system associated with the user’s vehicle) by the Access Terminal 250 to authenticate the user or vehicle for passage through the gateway. Successful authentication in this mannermay be required priorto opening one or both of the first gate system 230 or the second gate system 240.
FIG.3 illustrates an exemplary method 300 that may be performed in conjunction with the system 200 shown in FIG. 2. In this exemplary method, the control system 210 receives data (305) from the sensor system 220 that indicates the presence ofa vehicle seeking access through a gateway controlled by the first gate system 230 and second gate system 240. In response to receiving the sensor data, the control system 210 determines whether the second gate system 240 is closed (310). If the second gate system 240 is not closed (i.e.,a vehicle could drive through the second gate system 240) the control system 210 leaves the First Gate closed (315), which prevents multiple vehicles from tailgating past both the first gate system 230 and second gate system 240 as soon asthe first gate system 230 is opened.
If the control system 210 determines that the second gate system 240 is closed, the control system 210 opens (320) the first gate system 230 to allow the vehicle to pass the first gate system 230. The control system 210 attempts to close (325) the first gate system 230 behindthe vehicle after the vehicle passes the first gate system 230.
The control system 210 determines whether the first gate system 230 successfully closed behind the vehicle (330). If the first gate system230 successfully closed behind the vehicle, the vehicle will be positioned between the first gate system 230 and the second gate system 240 (both off which are closed) as shownforthe lead carin FIG. 4B. Any vehicles behind the lead vehicle (i.e., “Car B” in FIG. 4A) will be behind the first gate system 230. Li response to successfully closing the first gate system 230 behind the vehicle, the control system 210 authenticates the driver (or vehicle itself) (335) as described above. In response to a successful authentication, the control system 210 opens (340) the second gate system240 to allowthe vehicle to pass through the gateway, and closes (345) the second gate system 240 behind the vehicle.
In the event that the first gate system 230 did not close successfully, the control system may analyze (350) data from the sensor system 220 and generate an alarm (355). In The control system 210 may generate a variety of different alarms, such as visual alarms, audio alarms, and alarms included in electronic communications such as emails, SMS texts, and the like.
In order to prevent damage to longer vehicles, vehicles with trailers, or even a second vehicle attempting to tailgate behind a first vehicle, the control system 210 may refrain from closing either gate system 230, 240 in response to detecting an obstacle within a gate system. The control system may automatically analyze (350) sensor data to identify the nature of an obstacle. For example, in some embodiments the sensor system 220 may include one or more cameras positioned and adapted to capture an image (as well as video) of an obstacle blocking either gate system 230, 240. The control system 210 may then automatically identify the obstacle using, for example, an image recognition algorithm, and then generate the alarm (355) based on the identification of the obstacle.
For example, the subject matter and delivery of an alarm may be customized based on whether the obstacle is a person, animal, part ofa vehicle, another vehicle, etc. Consider an example where the obstacle is identified to be a second vehicle, the control system 210 may automatically determine that a vehicle is attempting to tailgate, and generate the alarm (355) to alerta user of the system 200 (such as a parking attendant) to attend to the gateway and enforce payment from the tailgating vehicle. The alarm could also (or alternatively) be delivered to the driver of the tailgating vehicle to instruct the driverof the second vehicle to backup to allowthe first gate system 230 to close. Alarms could also be generated and delivered toa law enforcement agency, as well as any other party.
In embodiments employingone or more cameras in conjunction with the sensor system 220, such cameras may be adapted to capture images of the drivers of vehicles attempting to pass through the gateway, as well as license plates coupledto such vehicles. The control system 210 may use image recognition algorithms or other techniques to determine whethera driver’s face and/or license plate is obscured from the view of the cameras. For example, a license plate may be covered in mud, or the driver may intentionally be hiding his/her face. Li such cases, an alarm may includ ea notification directed to the driver of a vehicle to remove the obfuscation to allow identification of the vehicle and/or driver.
For the sake of brevity, conventional data networking, application development and other functional aspects of the systems (and components of the individual operating components of the systems) may not be described in detail herein. Furthermore, the connecting lines shown in the various figures contained herein are intended to represent exemplary functional relationships and/or physical couplings betweenthe various elements. It should be noted that many alternative or additional functional relationships or physical connections may be present ina practical system.
The systems and methods ofthe present disclosure may be embodied as a customization of an existing system, an add-on product, a processing apparatus executing upgraded software, a stand alone system, a distributed System, a method, a data processing system,a device for data processing, and/or a computer program product. Accordingly, any portion of the system ora module may take the form of a processing apparatus executing code, an internet based embodiment, an entirely hardware embodiment, or an embodiment combining aspects of the internet, software and hardware. Furthermore, the system may take the form of a computer program product on a computer-readable storage medium having computer-readable program code means embodied inthe storage medium. Any suitable computer-readable storage mediummay be utilized, including hard disks, CD-ROM, optical storage devices, magnetic storage devices, and/or the like.

The more details on vehicle barrier system
1. A vehicle barrier system comprising:a sensor system for detectinga vehicle seeking passage through a gateway;
a first gate system;
a second gate system subsequent tothe first gate system; and
a control system in communication with the sensor system, the first gate system, and the second gate system, wherein the control system comprises:
a processor; and memory coupled to the processor and storing instructions that, when executed by the processor, cause the control system to:
receive data from the sensor system indicating the presence of the vehicle;
In response to receiving the sensor data indicating the presence ofthe vehicle, determine whetherthe second gate system is closed;
In response to determining that the second gate system is closed: open the first gate system to allow the vehicle to pass the first gate system; and attempt to close the first gate system behind the vehicle after the vehicle passes the first gate system;
In response to successfully closing the first gate system behind the vehicle, opening the second gate system to allow the vehicle to proceed through the gateway; and
In response to unsuccessfully closing the first gate system behind the vehicle, generating an alarm.
2. The system of claim 1, further comprising an accessterminal coupled to the control system and adapted toreceive input froma driver of the vehicle, wherein the memory of the control system further stores instructions for causing the control system to successfully authenticate the driver, based on the input from the driver, prior to opening the second gate system.
3. The system of claim 2, wherein the input from thedriver includes one or more of: insertion ofa validation ticket, entry ofa code, scanning ofa barcode, scanning of a radio frequency identification badge, and entry of biometric information.
4. The system of claim 2, wherein the sensor systemincludes one or more of:a camera,a motion sensor, apressure sensor, and an inductive loop sensor.
5. The system of claim 1, wherein the first gate systemcomprises one or more of:a horizontally tilting door,avertically tilting door,a sectional door,a vertically rotating arm, horizontally rotating arm, a spike barrier, and a post.
6. The system of claim 1, wherein thesecond gate systemcomprises one or more of:a horizontally tilting door, a vertically tilting door,a sectional door,a vertically rotating arm, horizontally rotating arm,a spike barrier, and a post.
7. The system of claim 1, wherein generating the alarmincludes generating one or more of:a visual alarm, an audioalarm, and an electronic communication.
8. The system of claim 1, wherein the sensor system isadapted to detect an obstacle blocking closure of the firstgate system, and wherein the memory of the control system further stores instructions for causing the control system to refrain from closing the first gate system in response to detection of the obstacle by the sensor system.
9. The system of claim 8, wherein the sensor systemincludes one or more cameras adapted to capture an imageof the obstacle blocking the first gate system.
10. The system of claim 9, wherein the memory ofthecontrol system further stores instructions for causing the control system to: automatically identify the obstacle from the image ofthe obstacle; and generate the alarm based on the identification of the obstacle.
11.The system of claim 11, wherein the obstacle isasecond vehicle, and wherein the memory ofthe controlsystem further stores instructions for causing the control system to: automatically identify the second vehicle from the image of the obstacle; and based on identifying the second vehicle, generate the alarm to a user of the system to attend to the gateway.
12. The system of claim 11, wherein the obstacle isasecond vehicle, and wherein the memory ofthe control system further stores instructions for causing the control system to: automatically identify the second vehicle from the image of the obstacle; and based on identifying the second vehicle, generate the alarm to instructa driver of the second vehicle to back up to allow the first gate system to close.
13. The system of claim 9, wherein the obstacle isasecond vehicle, and wherein the one or more cameras are adapted to capture one or more of: an image ofa driver of the vehicle, an image ofa driver of the second vehicle, an image of a license plate coupledtothe vehicle, and an image of a license plate coupled to the second vehicle.
14. The system of claim 13, wherein the memory of the control system further stores instructions for causing the control system to: determine, based on an image captured from theone or more cameras, that a license plate coupled to the vehicle is obscured; and generating an alarm directed to the driver of the vehicle that includes a notification that the license plate coupled to the vehicle is obscured.
15. A method comprising:receiving, bya control system, data from a sensor system indicating the presence ofa vehicle at a gateway, wherein the control system is in communication with the sensor system,a first gate system, anda second gate system that is subsequent to the first gate system; in response to receiving the sensor data indicating the presence of the vehicle, determining, by the control system, whether the second gate system is closed; in response to determining, by the control system, that the second gate system is closed: opening, by the control system, the first gate system to allow the vehicle to pass the first gate system; and attempting, by the control system, to close the first gate systembehindthe vehicle after the vehicle passes the first gate system; in response to successfully closing the first gate system behind the vehicle, opening, by the control system, the second gate system to allow the vehicle to proceed through the gateway; and in response to unsuccessfully closing the first gate system behind the vehicle, generating an alarm by the control system.
16. A tangible, non-transitory computer-readable medium storing instructions that, when executed by a control system in communication with a sensor system,a first gate system, and a second gate system that is subsequent tothe first gate system, cause the control system to: receive data from the sensor system indicating the presence of a vehicle at a gateway; in response to receiving the sensor data indicating the presence of the vehicle, determine whether the second gate system is closed; in response to determining that the second gate system is closed: open the first gate system to allow the vehicle to pass the first gate system; and attempt to close the first gate systembehindthe vehicle after the vehicle passes the first gate system; in response to successfully closing the first gate system behind the vehicle, opening the second gate system to allow the vehicle to proceed through the gateway; and in response to unsuccessfully closing the first gate system behind the vehicle, generating an alarm.
 Double Lane Full Height Turnstile Gate for Residential Area
Double Lane Full Height Turnstile Gate for Residential Area
 Dual Lane Tandem Full Height Turnstile Gate for Industry Park
Dual Lane Tandem Full Height Turnstile Gate for Industry Park
 Single Full Height Security Turnstile for Office Buildings
Single Full Height Security Turnstile for Office Buildings
 Motorised Double Full-Height Turnstile for Office Buildings
Motorised Double Full-Height Turnstile for Office Buildings

















Please leave a message if you are interested in this model