RFID turnstiles for regulating access in a transit system
What are RFID turnstiles?
The RFID Turnstiles have been in use for a long time. In the turnstile barrier gates, Radio Frequency Identification (RFID) credentials are presented at an RFID reader present in the gates. If the RFID credentials are determined to be valid, the gates open or else the gates do not open. To determine if the RFID credentials are valid, the RFID credentials have to pass a set of criteria set by service providers issuing the RFID credentials. The processing to be performed at the gate has to be quick so that the experience of passengers can be enhanced.
However, for faster processing of the RFID credentials, it entailed that the processing the RFID credentials are processed locally atthe gates rather than transmitting the credentials overthe internet. To ensure local processing, the gates should have enough storage capacity.
The turnstile security barriers have one or more techniques to validate RFID credentials from few digits of the RFID credentials presented at the RFID reader. Further, new guidelines entails using multiple digits to identify data associated with the RFID credentials. The multiple digits would entail additional amount of storage in the gates which can be solved by replacing the hardware in the gates. However, replacing the hardware would involve cost.
The entrance turnstiles comprise a movable barrier, secured storage, an RFID card reader,a first processing unit which reads a set of digits from RFID credential, generates and transmits a hash value ofthesetof digits and transmitsa first bin. The securirt turnstile gates comprise a memory, having a higher capacity than the secured storage, and a second processing unit, which sends validity information for a plurality of second bins having greater number of digits than the first bin, the validity information indicates which of the plurality of second bins is valid, check if the hash value is member of first list. If the hash value is on the first list, opening of the movable barrier is regulated and if a second bin from the plurality of second bins corresponding to the first bin is invalid, opening is denied.
In one embodiment, a entry turnstile gate for regulating access in a transit system is disclosed. It comprises a movable barrier, secured storage ona first circuit card,a RFID card reader coupled with the secured storage, a first processing unit coupled with the secured storage, wherein the first processing unit is configured to reada set of digits from RFID credential when the RFID credential is presented to the RFID card reader, generatea hash value of the set of digits, transmita first bin, wherein the first bin isa subset of the set of digits, and transmit the hash value of the set of digits,a memory on a second circuit card, wherein the memory has additional storage capacity than the secured storage, and a second processing unit coupled with the memory, whereinthesecond processing unit is configured to receive the first bin from the first circuit card, sends validity information for a plurality of second bins to the first card, wherein the validity information indicates which of the plurality of second bins is valid, the plurality of second bins each have a greater number of digits than the digits in the first bin, check ifthe hash value of the set of digits is a member of a list of a hash values of a plurality of unique-identification numbers associated with a plurality of RFID credentials present in the memory, wherein the list of the hash values ofthe plurality of unique-identification numbers indicate a list of RFID credentials that belong to a first list, the first processing unit configuredto regulate opening of the movable barrier depending on if the hash value of the set of digits is on the first list, and denythe opening ofthe movable barrier if a second bin from the plurality of second bins corresponding tothe first bin is invalid, i.e., if the 7-11 digits corresponding to the RFID credential are not valid foruse in the transportation system.
In another embodiment, the disclosure provides a method for regulating access in a transit system. The method comprises in a secured storage on a first circuit card, reading a set of digits from RFID credential when the RFID credential is presented to a RFID card reader, generating a hash value of the set of digits, transmittinga first bin, wherein the first bin is a subset of the set of digits, and transmitting the hash value of the set of digits, in a memory on a second circuit card, receiving the first bin from the first circuit card, sending validity information for a plurality of second bins to the first card, wherein the memory has additional storage capacity than the secured storage, the validity information indicates which of the plurality of second bins is valid, the plurality of second bins each havea greater numberof digits than the digits in the first bin, checking if the hash value of the set of digits is a member of a list of a hash values of a plurality of unique- identification numbers associated with a plurality of RFID credentials present in the memory, wherein the list of the hash values of the plurality of unique-identification numbers indicate a list of RFID credentials that belong to a first list, in the first circuit card, regulating opening of a movable barrier depending on if the hash value of the set of digits is on the first list, and denying the opening of the movable barrier ifa second bin from the plurality of second bins corresponding to the first bin is invalid, i.e., if the 7-11 digits corresponding to the RFID credential are not valid for use in the transportation system.
In yet another embodiment,a non-transitory computer-readable medium having instructions stored thereon, wherein the instructions, when executed by a plurality of processors, causes the plurality of processors to perform operations comprising in a secured storage ona first circuit card, reading a set of digits from RFID credential whenthe RFID credential is presented to a RFID card reader, generating a hash value of the set of digits, transmittinga first bin,
wherein the first bin is a subset of the set of digits, and transmitting the hash value of the set of digits, in a memory on a second circuit card, receiving the first bin from the first circuit card, sending validity information for a plurality of second bins to the first card, wherein the memory has additional storage capacity than the secured storage, the validity information indicates which of the plurality of second bins is valid, the plurality of second bins each have a greater number of digits than the digits in the first bin, checking if the hash value of the set of digits is a member of a list of a hash values of a plurality of unique-identification numbers associated with a plurality of RFID credentials present in the memory, wherein the list of the hash values of the plurality of unique-identification numbers indicate a list of RFID credentials that belong to a first list, in the first circuit card, regulating opening of a movable barrier depending on if the hash value of the set of digits is on the first list, and denying the opening of the movable barrier if a second bin from the plurality of second bins corresponding to the first bin is invalid.
Further areas of applicability of the present disclosure will become apparent from the detailed description provided hereinafter. It should be understood that the detailed description and specific examples while indicating various embodiments, are intended for purposes of illustration only and are not intended to necessarily limit the scope of the disclosure.
How do RFID turnstiles works?
The ensuing description provides preferred exemplary embodiment(s) only, and is not intended to limit the scope, applicability or configuration of the disclosure. Rather, the ensuing description of the preferred exemplary embodiment(s) will provide those skilled in the art with an enabling description for implementinga preferred exemplary embodiment.
Referring to FIG. 1, illustrates an exemplary embodiment of a transit system 100 according toan embodiment of the present disclosure. The transit system 100 shows a number of turnstile gate 102. A user 104 walks towards gate 102, presents RFID credentials at an RFID reader available at gate 102. If the RFID credentials are valid, the gate 102 opens and user 104 passes through. The RFID credentials can be in the form of an RFID card or can be stored on a smart device available with the user 104. The transit system 100 can be used forany public transport, for example, can be present at a bus station, railway station, etc.
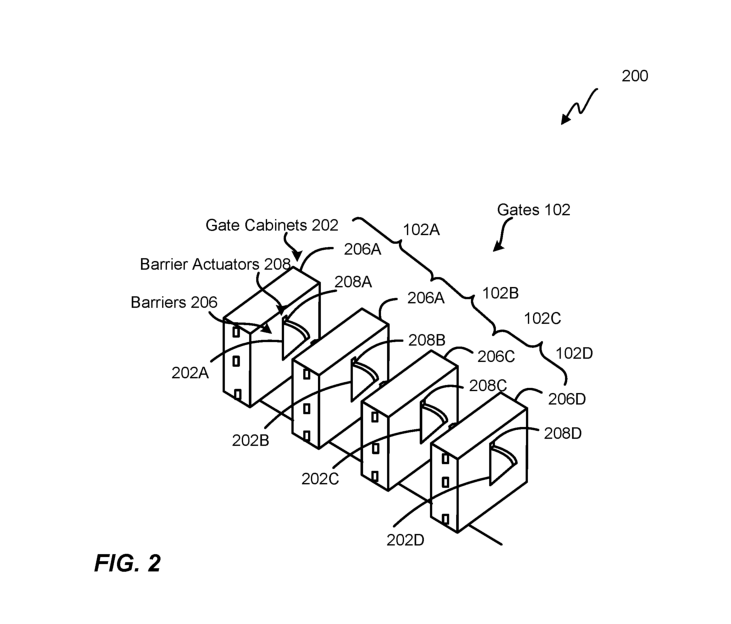
FIG.2 shows a perspective view of a gate array 200, according to an embodiment ofthe present disclosure. In general, the gate array 200 can be similar toa regular gate line used in transportation systems or environments. For example, the gate array 200 can include the number of RFID-enabled gate (102A, 102B, 102C, 102D) and gate cabinets 202 (202A, 202B, 202C, 202D) (or other types of entry points) which create passageways through the turnstile gate array 200. In some embodiments, the RFID-enabled gates 102 can comprise movable barriers 206 (206A, 206B, 206C, 206D). The movable barriers 206 can comprise various types of physical metal security gates to impede access to a restricted access area, such as turnstiles, sliding doors, boom gates, or gate barriers. In some embodiments, user 104 can swipe a ticket or card across an RFID card reader, for example, so that user 104 can pass through the movable barriers 206 to gain access to a restricted access area froma non-restricted access area. Such an implementation can generally be effective to prevent or at least hinder fare evasion. For example, when a particular ticket or card does not have sufficient funds or is invalid, the movable barrier 206 can remain closed to prevent the individual from entering or accessing the restricted access area. Movable barriers 206 associated with gate 102 can be opened up by a barrier actuator 208 (208A, 208B, 208C, 208D) to allow the user 104 passage upon successful validation of the RFID credentials by the RFID card reader.
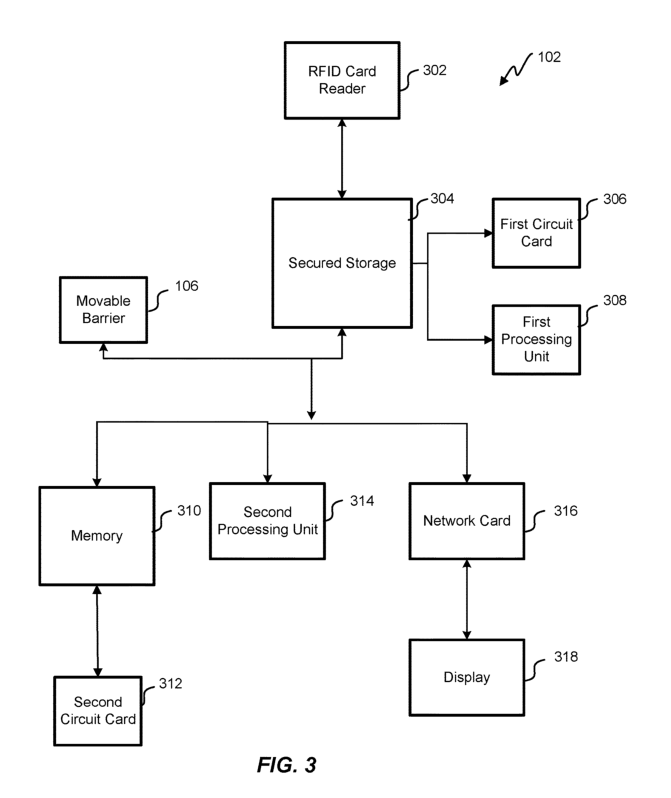
Referring to FIG.3 now, gate 102 for regulating access inthe transit system 100 is shown, according to some embodiments of the present disclosure. Gate 102 comprises the movable barrier 206, RFID card reader 302,a secured storage 304 ona first circuit card 306,a first processing unit 308 coupled withthe secured storage 304, a memory 310on a second circuit card 312, anda second processing unit 314 coupled with the memory 310. The RFID reader 302 used herein can refer to any communication device that can transmit and/or receive wireless signals to or from an RFID tag. The term “RFID reader” can be used interchangeably with the terms “RFID transceiver”, “RFID transmitter”, “RFID receiver”, “transceiver”, “transmitter”, “receiver”, “transmitter antenna”, “receiver antenna”, and “antenna”. For example, in embodiments where several transceivers are disclosed as being positioned alongthe side of a gate cabinet and/or entry point, some embodiments can include transmitters and/or receivers being positioned alongthe side of the gate cabinet. Similarly, in embodiments where several antennas are disclosed as being positioned along the side of a gate cabinet and/or entry point, some embodiments can include RFID transceivers, RFID transmitters, and/or RFID receivers as being positioned along the side of the gate cabinet and/or entry point.
The RFID reader 302 processes RFID credentials presented at the RFID reader 302 by the user 104 traveling using the transit system 100 and extractsa first set of digits from the RFID credentials. The RFID credentials can be in the form of RFID cards or can be stored ina smart device present with the user 104. The RFID card can bea prepaid card,a credit card, etc. The smart device can include a smart phone,a smart watch,a tablet,a laptop, etc. The RFID reader 302 applies radio-frequency identification (RFID) techniques to automatically identify RFID credentials. The RFID reader 302 is coupled with the secured storage 304. The secured storage 304 is present on a first circuit card 306. The first circuit card 306 can comprise of various electronic components for the functioning of the secured storage 304. For example, the first circuit card 306 can include transistors, resistors, etc. The secured storage 304 can be a volatile memory such as a flash memory,a random-access memory, etc. The secured storage 304 can be tamper proof i.e., stores sensitive information and requires protection of this information from attackers. The secured storage 304 ensures data security and integrity of RFID credentials.
The first processing unit 308 is coupled with the secured storage 304. The first processing unit 308 is configured to communicate with the secured storage 304 and process the data present on the secured storage 304. For example, the first processing unit 308 is configured to read the first set of digits from the RFID credentials when the RFID credentials are presented to the RFID reader 302. The first processing unit 308 is also configured to transmit a first Bank Identification Number (BIN) and transmit the first bin to the memory 310. The first bin is a subset of the set of digits of the RFID credentials which were read by the RFID card reader 302. The first bin is entailed by the banks to identify the type of RFID credentials. Further, the first processing unit 308 is configured to generate a hash value of the set of digits of the RFID credentials.
The memory 310 is storage that has additional storage capacity than the secured storage 304. For example, the memory 310 has three times additional capacity than the secured storage, however, is not limited. In various other embodiments, the memory 310 has10 time or more, 50 times or more, 100 times or more, 500 times or more, or 1000 times or more capacity than the secured storage. Thus, memory 310 stores additional data than the secured storage 304. The memory 310 is present on the second circuit card 312. The second circuit card 312 can be similar in construction to the first circuit card 306. Thus, the second circuit card 312 can also comprise transistors, resistors, etc.
The second processing unit 314 is coupled to the memory 310. The second processing unit 314 is configured to receive the first bin transmitted by the first processing unit 308. Further, the second processing unit 314 is configured to send validity information for a numberof second bins to the first circuit card 306. The validity information indicates which ofthe number of second bins are valid. The number of second bins each hasa larger number of digits than the first bin. In one embodiment, the second bin comprises of eight digits or 7-11 digits in various embodiments.
The validity of the RFID credentials can be determined by a service provider (for example,a bank) issuing the RFID credentials. For example, the service provider can issue multiple types of credentials to users. From the multiple types of credentials, the service provider can identify few credentials which are valid for transit systems and others which arenot valid for transit systems. Thus, the plurality of second bins helps identify which ofthe RFID credentials are of a valid type and which are not of valid types. The plurality of second bins indicates the type of RFID credentials that are not valid.
As the new payment guidelines require entail that the usage of 7-11 digits instead of 6 digits (as used earlier) to identify various details (including the validity) relating to the RFID credentials, the first processing unit 308 checks if the first bin is within a range of the plurality of second bins. Thus, ifthe first bin is withina range ofthe plurality of the second bins, it is determined that the RFID credentials presented atthe RFID reader 302 are invalid. Given this, the first processing unit 308 denies the opening of the movable barrier 206.
The second processing unit 314 is also configured to receive a hash value of the set of digits transmitted by the first processing unit 308. Further, the second processing unit 314 is configured to check if the hash value of the set of digits is a member of a list of hash values of a plurality of unique-identification numbers associated with a plurality of RFID credentials present in the memory, wherein the list of the hash values of the plurality of unique-identification numbers indicate a list of RFID credentials which belong to a first list.
Since the set of digits of the RFID credentials are considered to be secure, to transmit them outside of the secured storage 304, generation of the hash value of the set of digits of the RFID credentials is entailed. The generation of the hash value ensures that the set of digits of the RFID credentials are secured from attackers. A similar hashing algorithm is used by the second processing unit 314 to hash the list of hash values of the plurality of unique-identification numbers present in the memory 310. The plurality of unique-identification numbers are associated with the RFID credentials and indicate the unique-identification numbers belonging to a first list. The first list comprises the list of unique-identification numbers which are blacklisted by the service provider issuing the RFID credentials. The service provider can blacklist few RFID credentials based on multiple number of factors, for example, if the customer did not pay the bill on time or some fraudulent transactions have been detected by the service provider concerning the RFID credentials.
The number of entries in the first list can quite large, hence larger space for storage is entailed. Thus, the list is stored in memory 310 which has additional capacity than the secured storage 304. Further, the first list can be periodically updated by the service providers. For example, if a user has paid the bill associated with the RFID credentials, the first list can be updated by the service provider instantly i.e., the unique-identification number against which the bill has been paid is moved from the blacklisted to non-black-listed.
Thus, based on a determination if the hash value of the setof digits is on the first list, the first processing unit 308 regulates the opening of the movable barrier 206. For example, if the hash value of the set of digits is not present on the first list, i.e., the RFID credentials do not belong to the unique-identification number which is blacklisted, the first processing unit allows opening of the movable barrier 206. On the other hand, ifthe hash value of the set of digits is present on the first list, i.e., the RFID credentials belong to the unique-identification number which is blacklisted, the first processing unit denies opening of the movable barrier In one embodiment, the first list can be a list of unique-identification numbers which arenot blacklisted by the service providers issuing the RFID credentials. In that case, if the hash value of the set of digits is present on the first list, i.e., the RFID credentials do not belong to the unique-identification number which is blacklisted, the first processing unit permits opening of the movable barrier 206. On the other hand, ifthe hash value ofthe set of digits is not present on the first list, i.e., the RFID credentials belong to the unique-identification number which is blacklisted, the first processing unit denies opening of the movable barrier 206.
The processing of data by the first processing unit 308 and the second processing unit 314 including the reading of the RFID credentials by the RFID reader 302 is happening with a normal pace ofa user who desires to pass through gate 102 i.e., within an interval of half-second or even less. For example, an average usercan walk at a normal pace of 2 meters per second. However, the pace is not limited to 2 meters per second and may depend on height of the user. Gate 102 further comprisesa network card 316 that lets the gate 102 exchange data witha network over the internet. The data can be exchanged with servers of the service providers (for example banks). The data can include checking if the first list has been updated upon payment of the bills by the users. Gate 102 further comprises a display 318 which can be responsible for displaying information relating to the RFID credentials to user 104. The information can include balance associated with the RFID credentials, or an error message rejecting the RFID credentials, etc.
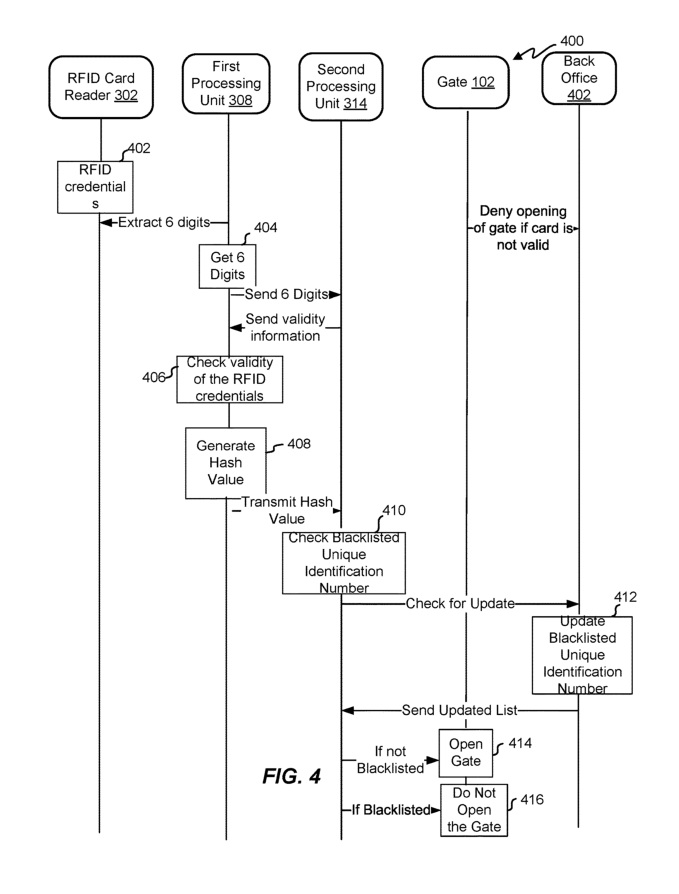
Referring to FIG.4 now,a swim diagram 400 showing communication between various entities are shown, in accordance with an embodiment of the present disclosure. The swim diagram 400 shows communication between the RFID card reader 302, the first processing unit 308, the second processing unit 314, the gate 102, and a back-office 402. The back-office 402 can be a cloud server of the service provider issuing the RFID credentials.
At block 402, the RFID credentials are presented at the RFID card reader 302.At block 404,6 digits of the RFID credentials are extracted and transmitted by the first processing unit 308 to the second processing unit 314. The second processing unit 314 sends validity information for 7-11 digits, depending on embodiment, tothe first processing unit 308. The validity information indicates which of the plurality of 7-11 digits in various embodiments is valid.
At block 406, the first processing unit 308 checks if the digits of the RFID credentials are in the range of the 7-11 digits (dependent on embodiment). Comparison with the 7-11 digits is done per the new payment guidelines. If the full digits are in the range of the 7-11 digits, the RFID credentials are considered to be invalid type. For example, one embodiment may have 8 digits for various bins where some are valid foruse in the transit system, while others are not such that the RFID credentials would not allow access to the transit system. If the RFID credentials is not of valid type, the first processing unit 308 denies opening of gate 102. In particular, the first processing unit 308 denies movement of the movable barrier 206.
At block 408, the first processing unit 308 generates a hash value of the digits of the RFID credentials. The RFID credentials are generally of 16 digits. In general, the digits of the RFID credentials are considered to be secured and are not to be shared with anyone for security purposes. Hence, the hash value is generated of the digits of the RFID credentials. The hash value of the digits of the RFID credentials is transmitted to memory 310.
At block 410, the second processing unit 314 checks if the hash value of the digits is a member of a list of hash values of a plurality of unique-identification numbers associated witha plurality of RFID credentials present in memory 310.
At block 412, the second processing unit 314 sends a command tothe back office 402 to check if there is any update in the first list. If there is any update, second processing unit 314 receives the updated first list. In another embodiment, the list of updated blacklisted unique-identification numbers is periodically updated and transmitted to the second processing unit 314 by the back office 402. If the hash value does not belong to the list of blacklisted unique-identification number, the first processing unit 308 (at block 414) send a command forthe opening of the gate 102. However, ifthe hash value belongs tothe list of blacklisted unique-identification number, the first processing unit 308 (at block 416), denies opening of the gate.
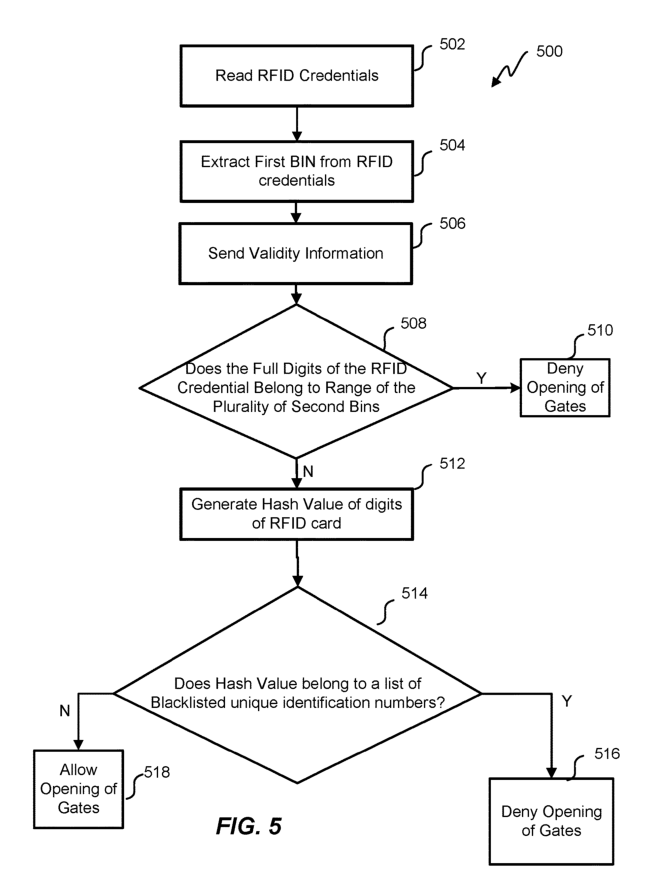
Referring to FIG.5 now,a flowchart of a method 500 for regulating access in the transit system 100 is disclosed, in accordance with some embodiment of the present disclosure. With the increase in the numberof digits entailed for verification of the RFID credentials as per the new payment guidelines, the storage entailed to store the digits also increases. Further, in the turnstile gate 102, it is entailed that the processing of the RFID credentials occurs as fast as possible such that the user presenting the RFID credentials at the gate does not have to wait for gate 102 to open. For this, the RFID credentials have tobe processed locally withno needtoneedto sendthe RFID credentials to the service providers through the internet.
The present disclosure ensures the processing of the RFID credentials occurs at gate 102 locally. The local processing of the RFID card ensures that gate 102 can open for the passenger the moment the passenger presents the RFID cardat gate 102, i.e., not create any delay. Further, the present disclosure ensures that the new payment guidelines are compiled with no requirement to modify the existing hardware.
At block 502, RFID credentials are read. The RFID credentials are read whena passenger willing to travel in public transport presents his/her RFID credentials at gate 102. The RFID credentials can be presented in the form of an RFID card or can be stored in a smart device present with the passenger. Gate 102 can be a turnstile gate i.e., instantly opens when the passenger presents the RFID card. The reading of the RFID credentials is performed by an RFID reader present inside gate 102. Once the RFID credentials are read, at block 504, a first bin is extracted fromthe RFID credentials by the first processing unit 308. The first bin or the first bank identification number is a number present in the RFID credentials Which are used by the service providers (for example, banks) to identify various information associated with the RFID credentials. In one embodiment, the first bin is the 6 digits of the RFID credentials. However, the first bin is not limited to the 6 digits and can include any number of digits except the total number of digits of the RFID credentials. The first bin is transmitted to the second processing unit 314.
At block 506, the method comprises sending the validity information for a plurality of second bins. The validity information is transmitted by the second processing unit 314 to the first processing unit 308. The validity information indicates which of the plurality of second bins are valid. In one embodiment, the plurality of second bins comprises 8 digits, but in other embodiments thebin is any integer between 7-11 digits.
At block 508, method 500 comprises determining if the digits of the RFID is in the range of the plurality of second bins i.e., determining if the 6 digits belong to the range of the 7-11 digits. The 7-11 digits can indicate which of the RFID credentials are considered invalid. The validity can be determined by the service provider issuing the RFID credentials. If the digits of the RFID belong tothe range of the plurality of second bins (i.e., “Y” at block 510), it is determined that the RFID credentials presented at the RFID reader are invalid and the opening of the movable barrier 206 present in the gate 102 is denied.
However, if the full digits of the RFID does not belong to the range of the plurality of second bins the method500 proceeds to block512 where a hash value of thefull number (i.e., all the digits) of the RFID credentials is generated. Since the full number of the RFID credentials is a secured number, the security of this number has to be maintained. Thus,a hash value is generated usinga hashing algorithm. The matching hashing algorithm is used to hash the list of blacklisted unique-identification numbers storedin memory 310. The list of unique-identification numbers indicates the list which is blacklisted by the service providers issuing the RFID credentials. The RFID credentials can be blacklisted by the service providers of the RFID card based on certain factors, such as bills not paid by the cardholder, cards involved in fraudulent transactions, etc.
At block 514, the first processing unit 308 checks if the hash value of the full numbers of the RFID card received by the first processing unit 308 belongs to the list of hash values of the RFID credentials stored in memory 310. This check indicates if the RFID credentials presented by the passenger at gate 102 are considered tobe blacklisted credentials by the service provider. If the credentials belong to the blacklisted list (block 516), the opening of the movable barrier 206 is denied or else the opening of the movable barrier 206 is permitted (block 518).
Brief description of the drawings for RFID turnstiles
The present disclosure is described in conjunction with the appended figures:
FIG.1 illustrates an exemplary embodiment of a transit system, in accordance with one embodiment of the present disclosure.
FIG.2 illustrates a perspective view of a gate array, in accordance with one embodiment ofthe present disclosure.
FIG.3 illustrates a modern gate turnstile for regulating access in a transit system, in accordance with one embodiment of the present disclosure.
FIG.4 illustrates a swim diagram showing communication between various entities in accordance with one embodiment ofthe present disclosure.
FIG.5 illustrates a flow diagram of a method for regulating access in a transit system, in accordance withone embodiment of the present disclosure.
In the appended figures, similar components and/or features may have the same reference label. Further, various components of the same type may be distinguished by following the reference label by a second alphabetical label that distinguishes amongthe similar components. If only the first reference label is used in the specification, the description is applicable to any one of the similar components having the same first reference label irrespective of the second reference label.

 Double Lane Full Height Turnstile Gate for Residential Area
Double Lane Full Height Turnstile Gate for Residential Area
 Dual Lane Tandem Full Height Turnstile Gate for Industry Park
Dual Lane Tandem Full Height Turnstile Gate for Industry Park
 Single Full Height Security Turnstile for Office Buildings
Single Full Height Security Turnstile for Office Buildings
 Motorised Double Full-Height Turnstile for Office Buildings
Motorised Double Full-Height Turnstile for Office Buildings















Please leave a message if you are interested in this model